Built-in protection for every drawing, file, and operation — so leadership stays audit-ready, and your team stays focused on manufacturing.
We protect your sensitive manufacturing data—from CAD drawings to G-code—across your entire production workflow. Built for defense contractors who need CMMC compliance without disrupting how they actually work.


Most manufacturing cybersecurity focuses only on protecting corporate networks—not the workflows, machines, and files that actually build the product. This creates blind spots in environments handling Controlled Unclassified Information (CUI), ITAR-restricted CAD drawings, and sensitive G-code.
Most cybersecurity protects your corporate network but ignores the actual production workflow—the CAD files, G-code, and machine communications that build your products.
Critical manufacturing data stays vulnerable while you struggle with compliance frameworks you can’t actually implement in your workflow.
We start where others stop—protecting your entire digital thread from engineering systems to CNC execution. Security that works with how you actually manufacture.
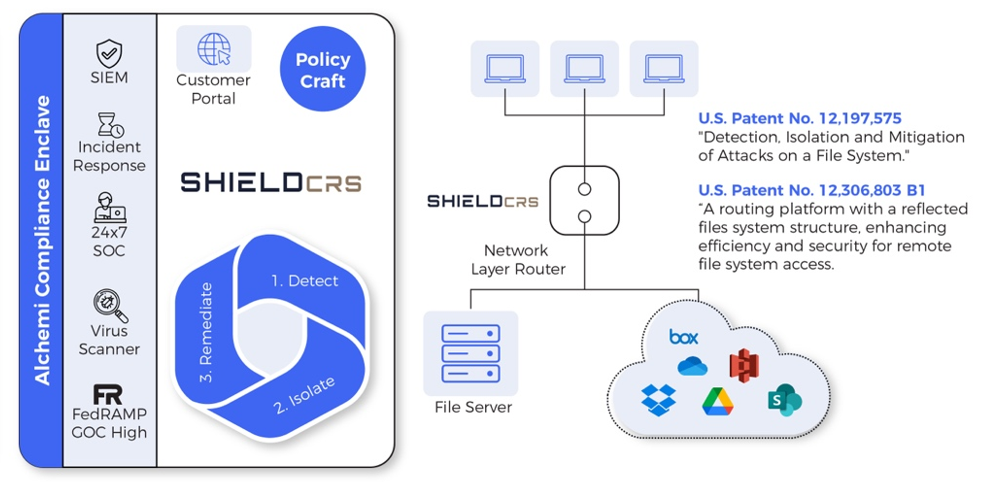
Alchemi Data brings together enclave-based infrastructure, real-time data protection, and automated compliance into one cohesive solution stack. Whether you're handling CUI, ITAR-controlled designs, or sensitive G-code, our platform protects your entire digital manufacturing workflow—from file creation to machine execution.

Securing your entire network for CMMC compliance. Every server, every endpoint, every connection becomes part of your audit scope. Massive complexity, massive cost.
The ACE Solution: Create a purpose-built vault just for your sensitive data. Your CUI gets its own secure enclave—dramatically shrinking your audit scope from everything to just what matters.
Intelligent insider threat detection that monitors your actual file access patterns and user behaviors, then automatically isolates threats and restores compromised files to their pre-attack state


Generic templates that don’t fit your setup, or expensive consultants who build policies from scratch. Either way, you’re stuck with policies that don’t match your actual environment.
PolicyCraft : Intelligent compliance automation that asks the right questions about your specific infrastructure, then builds policies tailored exactly to your setup—like TurboTax® for compliance.
Alchemi Data doesn't bolt on security after the fact—we embed it into every step of your production lifecycle. From the moment your designer creates a drawing to the final G-code release on the shop floor, every action is contained, monitored, and aligned with compliance frameworks like CMMC, ITAR, and NIST 800-171.
File Intake & Segmentation The moment files enter your system, Alchemi automatically separates sensitive CAD drawings and G-code from routine documents. No manual sorting, no missed classifications—just intelligent segregation that creates a clean audit trail from day one, so compliance officers never have to guess where sensitive data lives.
Quorum Approval for File Release No rogue engineer can push unauthorized files to production. Our multi-person approval system requires both technical and security sign-off before any sensitive file reaches the shop floor, automatically enforcing ITAR export controls and CMMC flow-down requirements without slowing down legitimate work.
PDM/MES Integration Alchemi enhances your existing WindChill, ENOVIA, or TeamCenter workflows without disrupting them. Your engineers keep using the tools they know while gaining the security and compliance layers that defense contracts demand—no retraining, no workflow changes, just better protection.
Secure Vault Storage Every CUI file lives in an encrypted vault with complete version history and cryptographic integrity. When auditors ask “Who modified this design and when?” you’ll have the answer instantly—not scattered across file servers and email chains, but in one traceable, defensible record.
Point-to-Point Machine Transfer Files move from vault to CNC machine through FIPS 140-2 certified channels—no USB drives, no network shares, no opportunities for interception. Every transfer is logged and verified, creating an unbreakable chain of custody that auditors love and attackers can’t compromise.
Full Isolation Within the Enclave CUI never leaves the protected environment. Engineers work through secure VDI, operators receive only authorized files, and even if someone’s laptop gets compromised, your manufacturing data stays locked in the vault. Complete containment, zero exposure.